What are the different types of EC2 instances based on their costs?
The four types of EC2 instances are:
On-demand Instance
It is cheap for a short time but not when taken for the long term
Spot Instance
It is less expensive than the on-demand instance and can be bought through bidding.
Reserved Instance
If you are planning to use an instance for a year or more, then this is the right one for you.
Dedicated Instance
A dedicated host is a physical server with EC2 instance capacity which is fully dedicated to your use. It can be purchased as a Reservation for up to 70% off On-Demand price.
What are the different types of instances?
Following are the types of instances:
- General purpose
- Computer Optimized
- Memory Optimized
- Storage Optimized
- Accelerated Computing
What is the difference between stopping and terminating an EC2 instance?
While you may think that both stopping and terminating are the same, there is a difference. When you stop an EC2 instance, it performs a normal shutdown on the instance and moves to a stopped state. However, when you terminate the instance, it is transferred to a stopped state, and the EBS volumes attached to it are deleted and can never be recovered.
Name the types of AMI provided by AWS
The types of AMI provided by AWS are:
- Instance store backed
- EBS backed
What is the boot time taken for the instance stored backed AMI?
The boot time for an Amazon instance store-backend AMI is less than 5 minutes.
What is the difference between EBS and Instance Store?
An Instance Store Volume is a temporary storage that is used to store the temporary data required by an instance to function. The data is available as long as the instance is running. As soon as the instance is turned off, the Instance Store Volume gets removed and the data gets deleted.
On the other hand, an EBS Volume represents a persistent storage disk. The data stored in an EBS Volume will be available even after the instance is turned off.
What are Solaris and AIX operating systems? Are they available with AWS?
Solaris is an operating system that uses SPARC processor architecture, which is not currently supported by the public cloud.
AIX is an operating system that runs only on Power CPU and not on Intel, which means that you cannot create AIX instances in EC2.
Since both operating systems have their limitations, they are not currently available with AWS.
How do you configure CloudWatch to recover an EC2 instance?
Here’s how you can configure them:
- Create an Alarm using Amazon CloudWatch
- In the Alarm, go to Define Alarm -> Actions tab
- Choose the Recover this instance option
How can you recover/log in to an EC2 instance for which you have lost the key?
If you’ve lost the key pair, you can create an AMI of the existing instance and launch a new one. You can then select a new key pair by following the instance launch wizard.
How can you add an existing instance to a new Auto Scaling group?
Here’s how you can add an existing instance to a new Auto Scaling group:
- Open EC2 console
- Select your instance under Instances
- Choose Actions -> Instance Settings -> Attach to Auto Scaling Group
- Select a new Auto Scaling group
- Attach this group to the Instance
- Edit the Instance if needed
- Once done, you can successfully add the instance to a new Auto Scaling group
How can you automate EC2 backup using EBS?
When doing an EC2 instance backup, you are essentially backing up the Elastic Block Store (EBS) volume (which contains all the data on it) by creating a snapshot of it. You can also create a new Amazon Machine Image (AMI) from your existing instance or a snapshot if needed.
3 Different Ways to Take EC2 Instance Backups
1) Automate Backups Using AWS Data Lifecycle Manager
In July of 2018, Amazon released Data Lifecycle Manager (DLM), a tool for automating EBS volumes. DLM allows you to use tag-based lifecycle policies to define various backup schedules.
The policy works by looking at the desired tags, so make sure your resources are tagged properly before starting.
2) Backup Automation Using AWS Backup
AWS Backup is a fully managed service that is used to automate backups on AWS (though it can be implemented on-premises as well, by using AWS Storage Gateway). Compared to Data Lifecycle Manager, it is a much more powerful tool, and it can serve as a centralized location for configuring and monitoring backups.
AWS Backup can be used not only for an EBS volume, but also for RDS databases, DynamoDB tables, Storage Gateway volumes, and even EFS file systems.
3) Schedule Automated Amazon EBS Snapshots Using CloudWatch Events
The last backup method we will examine is EBS Snapshot creation using CloudWatch events. To implement this process, you will use a CloudWatch rule.
This will give you two options: you can either have this rule triggered using a fixed rate (every X minutes, hours, or days), or you can use a cron expression, which gives you much more flexibility. For example, you can have an event that triggers every Wednesday, Thursday, and Friday at 6pm. You will also see a preview of your next ten trigger dates. Do note that all times are presented in GMT.
After configuring the desired schedule, click on Add Target and chose “EC2 CreateSnapshot API call” from the list. Then, copy the volume ID of the volume you want to backup. You can leave the option to create a new role, unless you have one already.
Click on Configure details, name your rule, and give it a description. After that, you are ready to go.
How do you auto-delete old snapshots?
To delete snapshots you can simply use a bash script that will fetch all the snapshot ids older than 10 days and then can delete them using the AWS CLI command.
To find all the snapshots created before a particular timestamp (say some date):
(The jq filter as written will output JSON into the resulting file. You need to add another filter to extract just the desired.snapshot ID field and you’d probably want to pipe that into sed to strip the double quotes. I believe the AWS command also requires a region. And finally, flip the greater/less if you want to remove older snapshots. )
aws ec2 describe-snapshots –region=’region-name’ –owner self –output json | jq ‘.Snapshots[] | select(.StartTime < “2021-04-27”) | .SnapshotId’ | sed ‘s/”//g’ > snap_list.txt
Use for loop to delete all the snapshots from the list generated one by one.
for snap_id in `cat snap_list.txt`
do
aws ec2 delete-snapshot –snapshot-id $snap_id
done
You can also simply use the snapshot retention period in AWS for snapshot automatic deletion.
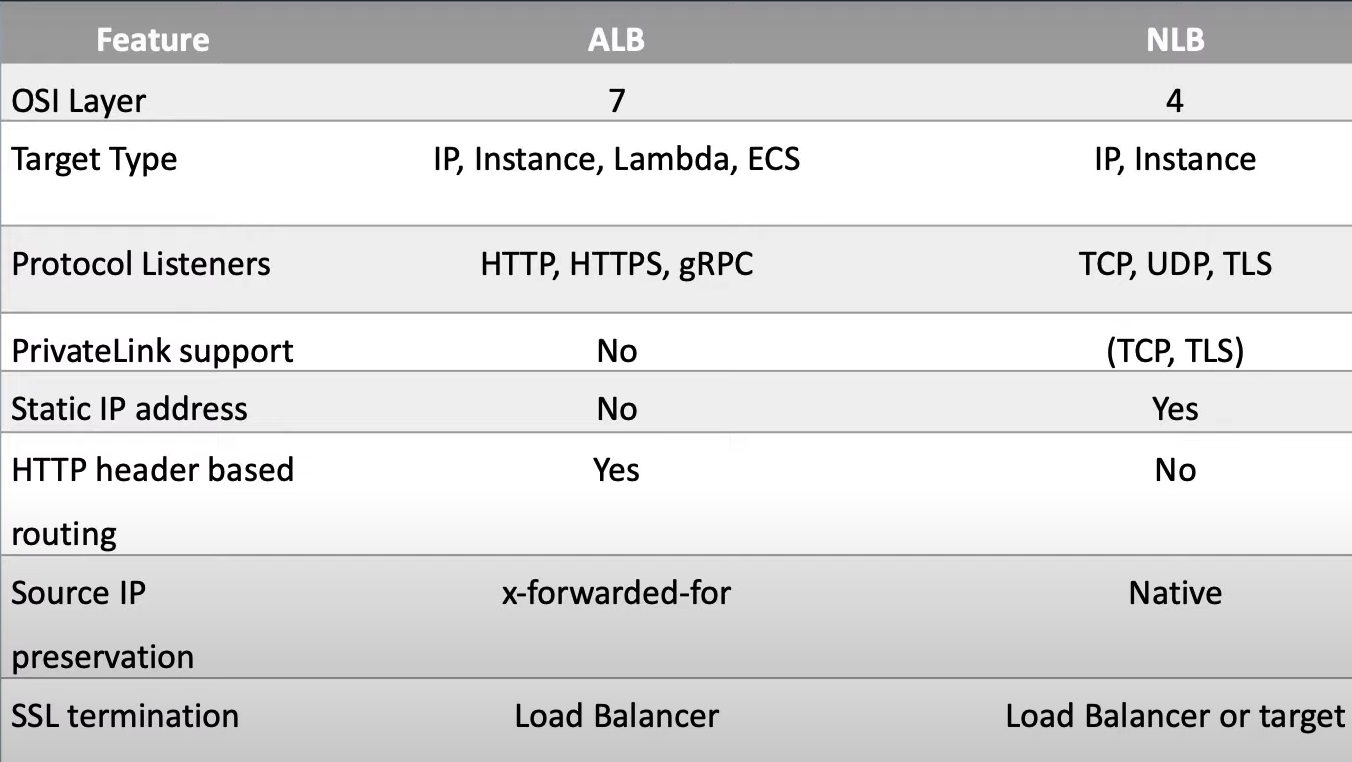
What are the different types of load balancers in AWS?
There are four types of load balancers that are supported by Elastic Load Balancing:
- Application Load Balancer
- Network Load Balancer
- Gateway Load Balancer
- Classic Load Balancer (previous generations)
What are the different uses of the various load balancers in AWS Elastic Load Balancing?
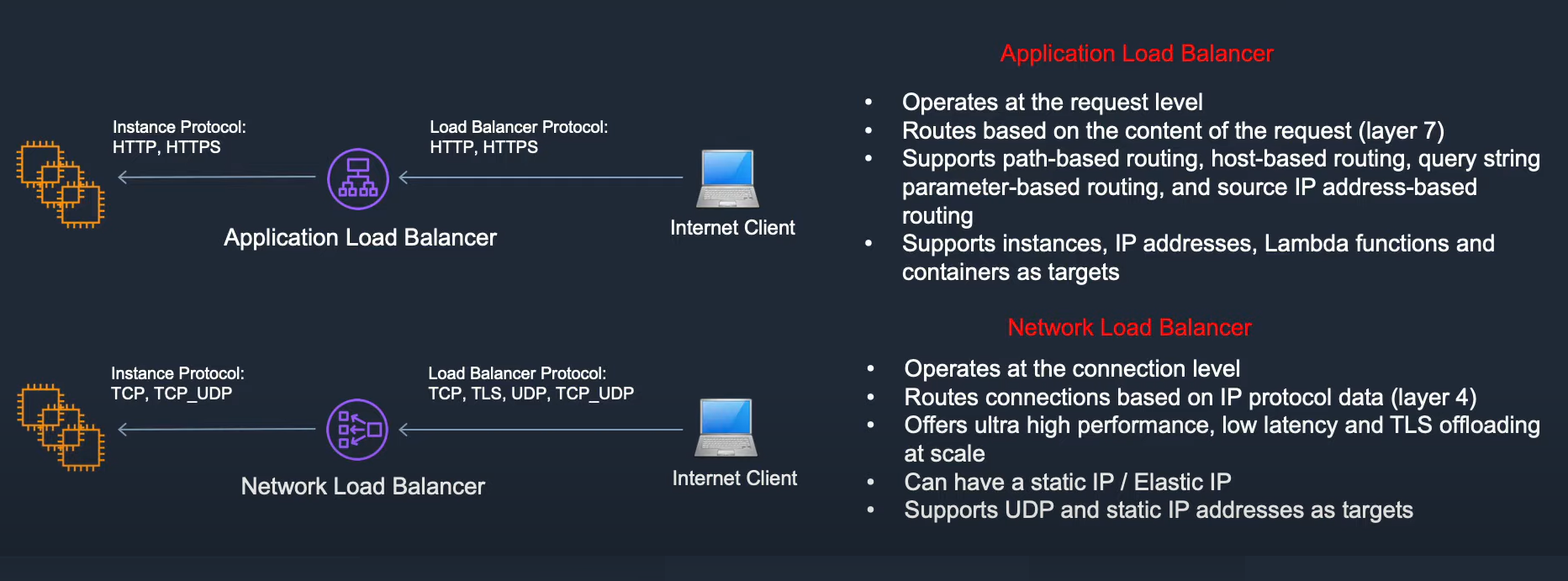
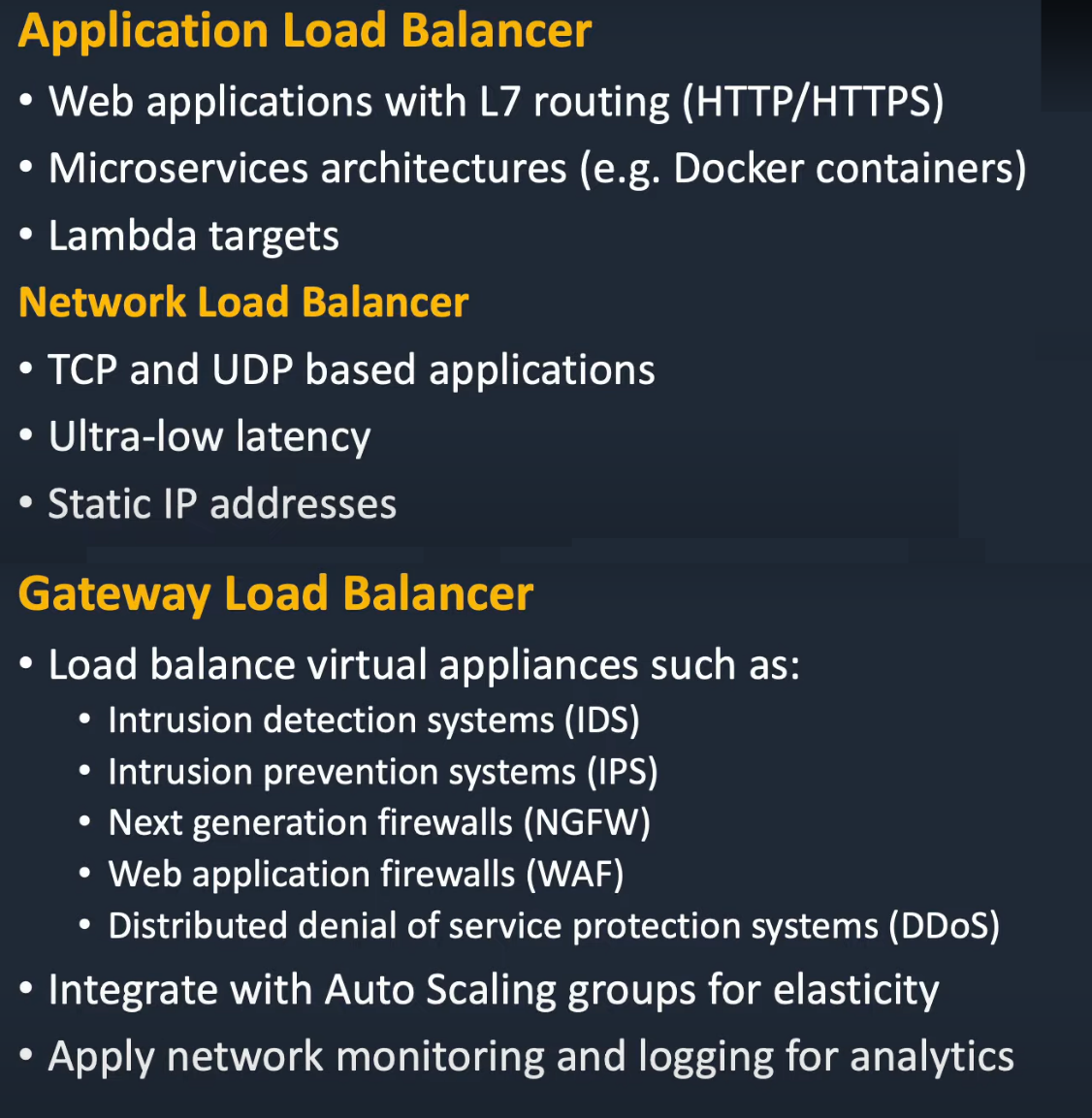
Application Load Balancer
Used if you need flexible application management and TLS termination.
Network Load Balancer
Used if you require extreme performance and static IPs for your applications.
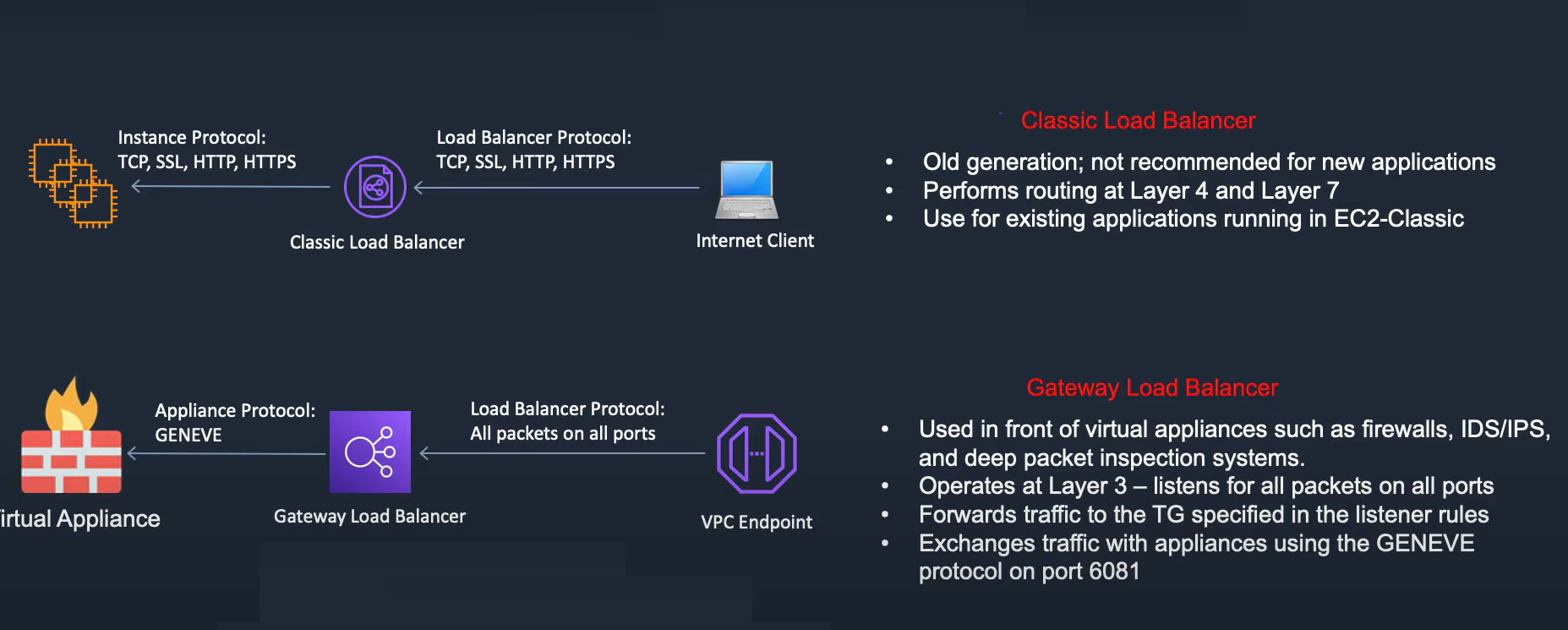
Gateway Load Balancer
Gateway Load Balancer helps you easily deploy, scale, and manage your third-party virtual appliances. It gives you one gateway for distributing traffic across multiple virtual appliances while scaling them up or down, based on demand.
Classic Load Balancer
Used if your application is built within the EC2 Classic network
When should you use the classic load balancer and the application load balancer?
The classic load balancer is used for simple load balancing of traffic across multiple EC2 instances.
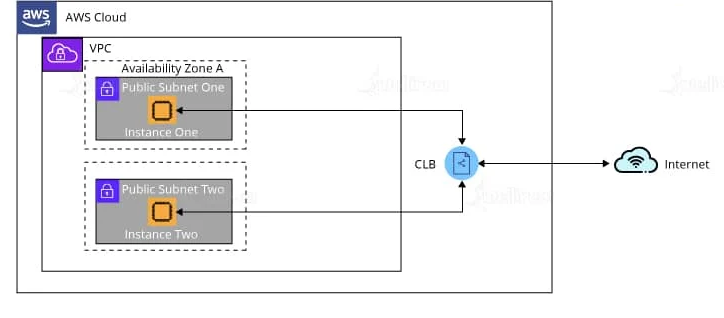
While, the application load balancing is used for more intelligent load balancing, based on the multi-tier architecture or container-based architecture of the application. Application load balancing is mostly used when there is a need to route traffic to multiple services.
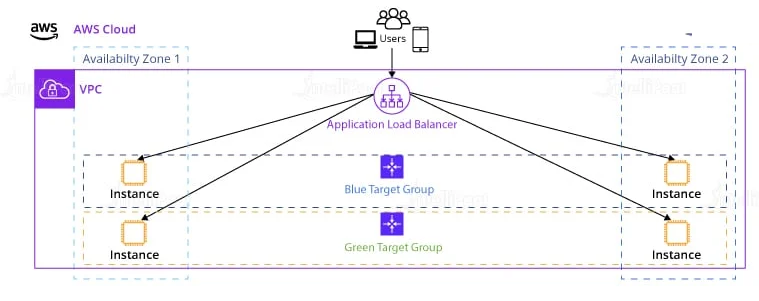
You have connected four instances to ELB. To automatically terminate your unhealthy instances and replace them with new ones, which functionality would you use?
Auto-scaling groups
What do you understand by a Security Group?
A security group acts as a virtual firewall for your EC2 instances to control incoming and outgoing traffic. Inbound rules control the incoming traffic to your instance, and outbound rules control the outgoing traffic from your instance. When you launch an instance, you can specify/select security groups.
Can you change the Private IP Address of an EC2 instance while it is running or in a stopped state?
No, a Private IP Address of an EC2 instance cannot be changed. When an EC2 instance is launched, a private IP Address is assigned to that instance at the boot time. This private IP Address is attached to the instance for its entire lifetime and can never be changed.
Explain if you can vertically scale an Amazon instance. How?
- Open the Amazon EC2 console.
- In the navigation pane, choose Instances, and select the instance.
- Choose Actions, select Instance State, and then choose Stop.
- With the instance still selected, choose Actions, select Instance Settings, and then choose Change Instance Type. Note that this action is disabled if the instance state is notstopped.
- In the Change Instance Type dialog box, do the following:From Instance Type, select the instance type that you want. If the instance type that you want does not appear in the list, then it is not compatible with the configuration of your instance (for example, because of virtualization type).(Optional) If the instance type that you selected supports EBS–optimization, select EBS-optimized to enable EBS–optimization or deselect EBS-optimized to disable EBS–optimization. Note that if the instance type that you selected is EBS–optimized by default, EBS-optimized is selected and you can’t deselect it.Choose Apply to accept the new settings.
- To restart the stopped instance, select the instance, choose Actions, select Instance State, and then choose Start.
- In the confirmation dialog box, choose Yes, Start. It can take a few minutes for the instance to enter the running state.
How to mount a volume to an instance:
Create volume from a snapshot
Create new instance
Attach the volume to the instance – both should be in the same zone
Then do lsblk and check the new volume attached ( lsblk ignores /dev while listing volume)
Create a new_volume directory in the Linux box to mount the volume
Mount cmd: – mount /dev/xvdf /newvolume_directory
Run just “mount” command (command to see your mounted volume and its details)
If you want to have a logical volume to be mounted automatically on boot, add the below line in /etc/fstab. You need to specify the file system type (e.g., EXT4) of the volume, which you can find out from the output of the mount command above.
/dev/nfsvolume/nfs /newvolume ext4 defaults 0 0 ( this is below line )
————-
To mount jenkins backed-up snapshot volume we need to use the command:
mount /dev/nfsvolume/nfs /newvolume/ ( As it is lvm partition in linux)
——— How to mount an LVM partition on Linux
$ mount /dev/sdb2 /mnt
mount: unknown filesystem type ‘LVM2_member’
$ sudo pvs
PV VG Fmt Attr PSize PFree
/dev/sdb2 vg_ezsetupsystem40a8f02fadd0 lvm2 a– 237.60g 0
sudo lvdisplay <volume-group-name>
$ sudo lvdisplay /dev/vg_ezsetupsystem40a8f02fadd0 ( /dev/vg_ezsetupsystem40a8f02fadd0 is volume group name which we get from “pvs” command)
sudo mount /dev/vg_ezsetupsystem40a8f02fadd0/lv_home /mnt (where lv_home is “LV name” which we get from lvdisplay command)
mount /dev/nfsvolume/nfs /newvolume/ — in case of jenkins backed snapshot
While connecting to your instance what are the possible connection issues one might face?
The possible connection errors one might encounter while connecting instances are
- Connection timed out
- User key not recognized by the server
- Host key not found; permission denied
- An unprotected private key file
- Server refused our key or No supported authentication method available
- Error using MindTerm on Safari Browser
- Error using Mac OS X RDP Client
The data on the root volumes of store-backed and EBS-backed instances get deleted by default when they are terminated. If you want to prevent that from happening, which instance would you use?
EBS-backed instances. EBS-backed instances use EBS volume as their root volume. EBS volume consists of virtual drives that can be easily backed up and duplicated by snapshots.
The biggest advantage of EBS-backed volumes is that the data can be configured to be stored for later retrieval even if the virtual machine or the instances are shut down.
You accidentally stopped an EC2 instance in a VPC with an associated Elastic IP. If you start the instance again, what will be the result?
Elastic IP will be only disassociated from the instance if it’s terminated. If it’s stopped and started, there won’t be any change to the instance and no data will be lost.
Explain Public IP, Private IP, and Elastic IP
Public DNS/IP: It is allocated from a pool of available IPs and it is mandatory to let you connect from anywhere around the globe to your EC2 instance.
Private IP: Its allocation is based on vpc/subnet in which EC2 is set up. Every subnet has a range of IPs, out of which one IP gets allocated to the launched EC2. The scope or visibility of this IP is only under the defined VPC. Hence, to communicate between two or more EC2 instances using private IP, all must be under the same vpc.
Note: Private IP designated to an EC2 remains same until vpc is same.
Elastic IP: – It is similar to static IP and can be assigned to any EC2 instance. Once we assign it, the existing public IP gets released and replaced with the newly assigned Elastic IP. They are allocated to the AWS account so that we can release it from specific EC2 and re-assign it to any other EC2 instances (if needed).
- There are many reasons why we should use Elastic IP. For example – Public IP & DNS record changes if we stop-start an instance. This would lead to a non-functional website until DNS records are re-updated. To avoid such issues, we make use of Elastic IP.
Path: AWS console -> EC2 -> Network & Security -> Elastic IP’s
To assign an Elastic IP, navigate to the above path and click on ‘Allocate New Address, followed by specifying the required EC2 instance.
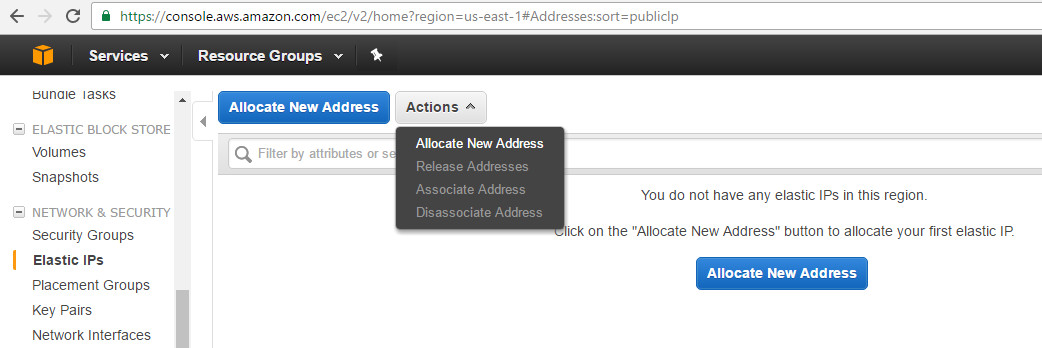
Elastic IP can be dissociated anytime per need. Once dissociated, AWS re-assign a new public IP from its pool whereas Elastic IP gets listed in dissociated IP list.
Effects of Restart | stop-start | terminate of EC2 instances on IP addresses:
- Restart of EC2: All 3 IPs remain the same as virtual machines remain unchanged.
- Stop-Start: Existing Public IP is released as AWS takes away the VM. On start, a new public IP/VM is provisioned. It is validated only for EBS-backed AMI. Private IP remains the same, whereas if an EC2 is designated with Elastic IP, both Elastic/Public IPs will remain the same.
- Terminate: Both Public and Private IP are released, whereas Elastic IP gets dissociated, which can be associated again with any other EC2 instance.
What does an AMI include?
An Amazon Machine Image (AMI) is a template that contains a software configuration (for example, an operating system, an application server, and applications). From an AMI, you launch an instance, which is a copy of the AMI running as a virtual server in the cloud.
What Are Some of the Security Best Practices for Amazon EC2?
For secure Amazon EC2 best practices, follow the following steps
- Use AWS identity and access management to control access to your AWS resources
- Restrict access by allowing only trusted hosts or networks to access ports on your instance
- Review the rules in your security groups regularly
- Only open permissions that you require
- Disable password-based login, for example, launched from your AMI
What is fleet management in Amazon EC2 Auto Scaling?
Amazon EC2 auto-scaling service continuously monitors the health of Amazon EC2 instances and other applications. When EC2 auto-scaling identifies unhealthy instances, it automatically replaces the unhealthy EC2 instances with new EC2 instances.
Also, this service ensures the seamless running of applications and balances EC2 instances across the zones in the cloud.
I created a web application with autoscaling. I observed that the traffic on my application is the highest on Wednesdays and Fridays between 9 AM and 7 PM. What would be the best solution for me to handle the scaling?
Configure a policy in autoscaling to scale as per the predictable traffic patterns.
You have an application running on your Amazon EC2 instance. You want to reduce the load on your instance as soon as the CPU utilization reaches 100 percent. How will you do that?
It can be done by creating an autoscaling group to deploy more instances when the CPU utilization exceeds 100 percent and distributing traffic among instances by creating a load balancer and registering the Amazon EC2 instances with it.
Suppose, you hosted an application on AWS that lets the users render images and do some general computing. Which of the below-listed services can you use to route the incoming user traffic?
- Classic Load Balancer
- Application Load Balancer
- Network Load balancer
Application Load Balancer: It supports path-based routing of the traffic and hence helps in enhancing the performance of the application structured as smaller services.
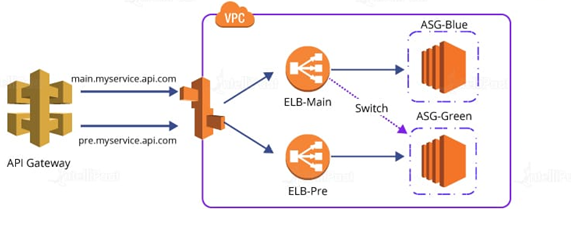
Using an application load balancer, the traffic can be routed based on the requests made. In this case scenario, the traffic where requests are made for rendering images can be directed to the servers only deployed for rendering images and the traffic where the requests are made for computing can be directed to the servers deployed only for general computing purposes.
Is it possible to switch from an Instance-backed root volume to an EBS-backed root volume at any time?
No, it is not possible.
Can you change the instance type of the instances that are running in your application tier and are also using autoscaling? If yes, then how? (Choose one of the following)
– Yes, by modifying autoscaling launch configuration
- Yes, by modifying autoscaling tags configuration
- Yes, by modifying autoscaling policy configuration
- No, it cannot be changed
Yes, the instance type of such instances can be changed by modifying the autoscaling launch configuration. The tags configuration is used to add metadata to the instances.
You want to modify the security group rules while it is being used by multiple EC2 instances. Will you be able to do that? If yes, will the new rules be implemented on all previously running EC2 instances that were using that security group?
Yes, the security group that is being used by multiple EC2 instances can be modified. The changes will be implemented immediately and applied to all the previously running EC2 instances without restarting the instances.
What is a Launch Template and difference between a Launch Template and a Launch Configuration?
A launch template is merely a group of all the configurations that create and configure an EC2 instance. Likely, you would have already walked through creating one EC2 instance using that EC2 wizard. And that’s wonderful for making your first instance, but if you have to create thousands of instances? Do you really enjoy to be going through that wizard every single time? I don’t, and you probably don’t want to either.
So what the launch template does is step through that wizard and effectively just save the results, creating a template with all configurations in a single place, so when we need that to create a new instance again, we can just push that button. The instance is created precisely as we’ve defined it in that template. If you’ve touched on auto-scaling before, you might think that this launch template looks a lot like a launch configuration. And it’s. So let’s compare the launch template vs a launch configuration.
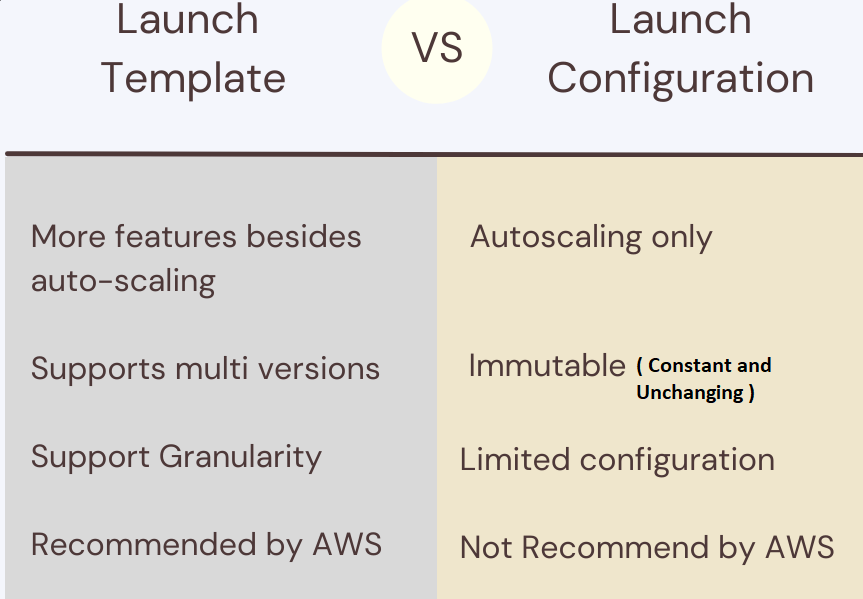
The launch templates are more recent, practical, quicker, and powerful options. It’s just the most suitable. It doesn’t imply that you’re technically incorrect if you’re utilizing a launch configuration. It’s just AWS has released the launch templates, and they deliver us extra flexibility and instruments that the launch configuration didn’t. So the launch templates, as we’ll notice in the table above, are for more than only auto-scaling. This permits us to operate that template at any moment, compared to those launch configurations, which are just for auto-scaling those EC2 instances. Also, the launch templates support versioning. This indicates that we can efficiently design unique versions, new revisions, or perhaps we have got new user_data, a fresh AMI image, and it’s all held in one single location.
What are sticky sessions, how do I know if a sticky session is enabled in the load balancer?
The sticky session feature (also known as session affinity) is to enable the load balancer to bind a user’s session to a specific target. This ensures that all requests from the user during the session are sent to the same target.
In case of Sticky Sessions, all your requests will be directed to the same physical web server while in case of a non-sticky load balancer may choose any webserver to serve your requests.
To check if sticky session is enabled:
On the navigation pane, under Load Balancing, choose Load Balancers.
Select your load balancer.
On the Description tab, choose Edit stickiness.
On the Edit stickiness page, select Enable application-generated cookie stickiness.
Why should you avoid sticky sessions?
They can make our application go down easily
Imagine that one of our servers goes down. Because of the architecture we chose to follow, even if we use persistent storage like HDD for example, to keep our application’s state, we won’t be able to access this data from other servers. Furthermore, if we use the application’s memory as our state storage, we are doomed to lose all data that were bound to this server’s sessions in case of a server restart.
What is ELB Connection Draining?
With the Connection Draining feature enabled if an EC2 backend instance fails health checks the Elastic Load Balancer will not send any new requests to the unhealthy instance. However, it will still allow existing (in-flight) requests to complete for the duration of the configured timeout.
Enabling this feature will allow better management of the resources behind the Elastic Load Balancer, such as replacing backend instances without impacting the user experience. For example, taking an instance out of service and replacing it with a fresh EC2 instance that contains updated software, while avoid breaking open network connections.
To enable connection draining using the console
Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
On the navigation pane, under Load Balancing, choose Load Balancers.
Select your load balancer.
On the Instances tab, for Connection Draining, choose (Edit).
On the Configure Connection Draining page, select Enable Connection Draining.
(Optional) For Timeout, type a value between 1 and 3,600 seconds.
Choose Save.