Resources covered:
IAM| EC2 | JENKINS | TERRAFORM |
JENKINS:
Jenkins is an open-source automation server used for Continuous Integration and Continuous Deployment (CI/CD). It helps automate building, testing, and deploying software projects. Jenkins is highly extensible, features a web-based interface, supports distributed builds, and has a large community with numerous plugins for integrating with various tools and services. It plays a key role in streamlining and automating software development workflows.
Steps :
Step 3: Run the terraform script
Step 4: Complete the Initial steps by browsing with URL <ip:8080>
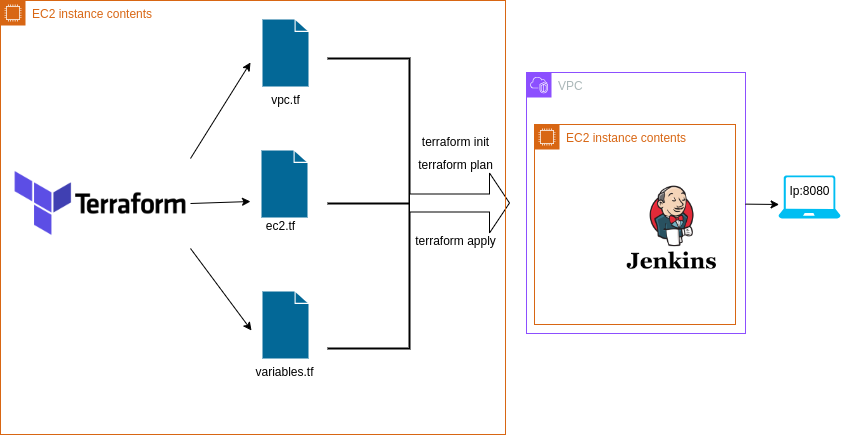
Step 1: Create a role with AWS admin access then create an ec2 instance (client-machine) and attach the role to the client machine and install terraform on that machine
Step 2: Create a Directory named Jenkins_ec2 and create a files as shown below
mkdir Jenkins_ec2 # creates a Directory
cd Jenkins_ec2 create vpc.tf
vi vpc.tf
#copy the below code
provider "aws" {
region = var.region
}
# Create VPC
resource "aws_vpc" "jenkins_vpc" {
cidr_block = "10.0.0.0/16"
enable_dns_support = true
enable_dns_hostnames = true
tags = {
Name = "JenkinsVPC"
}
}
# Internet gateway
resource "aws_internet_gateway" "gw" {
vpc_id = aws_vpc.jenkins_vpc.id
tags = {
Name = "JenkinsIGW"
}
}
# Create public route table
resource "aws_route_table" "public_route_table" {
vpc_id = aws_vpc.jenkins_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.gw.id
}
tags = {
Name = "PublicRouteTable"
}
}
# Associate the route table with the public subnet
resource "aws_route_table_association" "public_subnet_association" {
subnet_id = aws_subnet.public_subnet.id # Replace with your public subnet ID
route_table_id = aws_route_table.public_route_table.id
}
# Create public subnet
resource "aws_subnet" "public_subnet" {
vpc_id = aws_vpc.jenkins_vpc.id
cidr_block = "10.0.1.0/24"
availability_zone = var.az #
map_public_ip_on_launch = true
tags = {
Name = "PublicSubnet"
}
}
# Create security group
resource "aws_security_group" "jenkins_sg" {
vpc_id = aws_vpc.jenkins_vpc.id
name = "jenkins_sg"
description = "Allow inbound traffic on port 8080 and 22 for Jenkins"
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 8080
to_port = 8080
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
create ec2.tf file
# IAM Role with Administrator Access
resource "aws_iam_role" "admin_role" {
name = "admin-role"
assume_role_policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
EOF
}
# Administrator Access Policy
resource "aws_iam_policy" "admin_policy" {
name = "admin-policy"
description = "Administrator Access Policy"
policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
EOF
}
# Attach Administrator Access Policy to IAM Role
resource "aws_iam_role_policy_attachment" "admin_attachment" {
policy_arn = aws_iam_policy.admin_policy.arn
role = aws_iam_role.admin_role.name
}
resource "aws_iam_instance_profile" "admin_instance_profile" {
name = "admin-instance-profile"
role = aws_iam_role.admin_role.name
}
# Provisioning Jenkins on the EC2 instance using user_data
resource "aws_instance" "jenkins_instance" {
ami = var.ami_id
instance_type = var.instance_type
key_name = var.key_name
subnet_id = aws_subnet.public_subnet.id
user_data = <<-EOF
#!/bin/bash
sudo yum update -y
sudo amazon-linux-extras install java-openjdk11 -y
sudo wget -O /etc/yum.repos.d/jenkins.repo https://pkg.jenkins.io/redhat/jenkins.repo
sudo rpm --import https://pkg.jenkins.io/redhat-stable/jenkins.io-2023.key
sudo yum install -y jenkins
sudo systemctl start jenkins
sudo systemctl enable jenkins
EOF
vpc_security_group_ids = [aws_security_group.jenkins_sg.id]
iam_instance_profile = aws_iam_instance_profile.admin_instance_profile.name
depends_on = [aws_iam_role.admin_role]
tags = {
Name = var.instance_name
}
}
create variables.tf
vi variables.tf
#copy the below code
variable "region" {
description = "aws region to use"
type = string
}
variable "az" {
description = "avaliabilty zone"
type = string
}
variable "ami_id" {
description = "ami id of instance"
type = string
}
variable "key_name" {
description = "key pair"
type = string
}
variable "instance_type" {
description = "instance type"
type = string
}
variable "instance_name" {
description = "instanc name"
type = string
}
create values.tfvars
vi values.tfvars
#copy below code
region = "us-east-1"
az = "us-east-1a"
ami_id = "ami-00b8917ae86a424c9"
key_name = "new"
instance_type = "t2.micro"
instance_name ="jenkins_machine"
Step 3: Run the terraform script
follow the below commands from your directory where your .tf files are located
terraform init
terraform apply -var-file=values.tfvars
Step 4: Complete the Initial steps by browsing with URL <ip:8080>
Open Browser >> browse your public ip on port 8080 <ip:8080> and complete the initial steps and Create First Admin User
Jenkins by default runs on port 8080
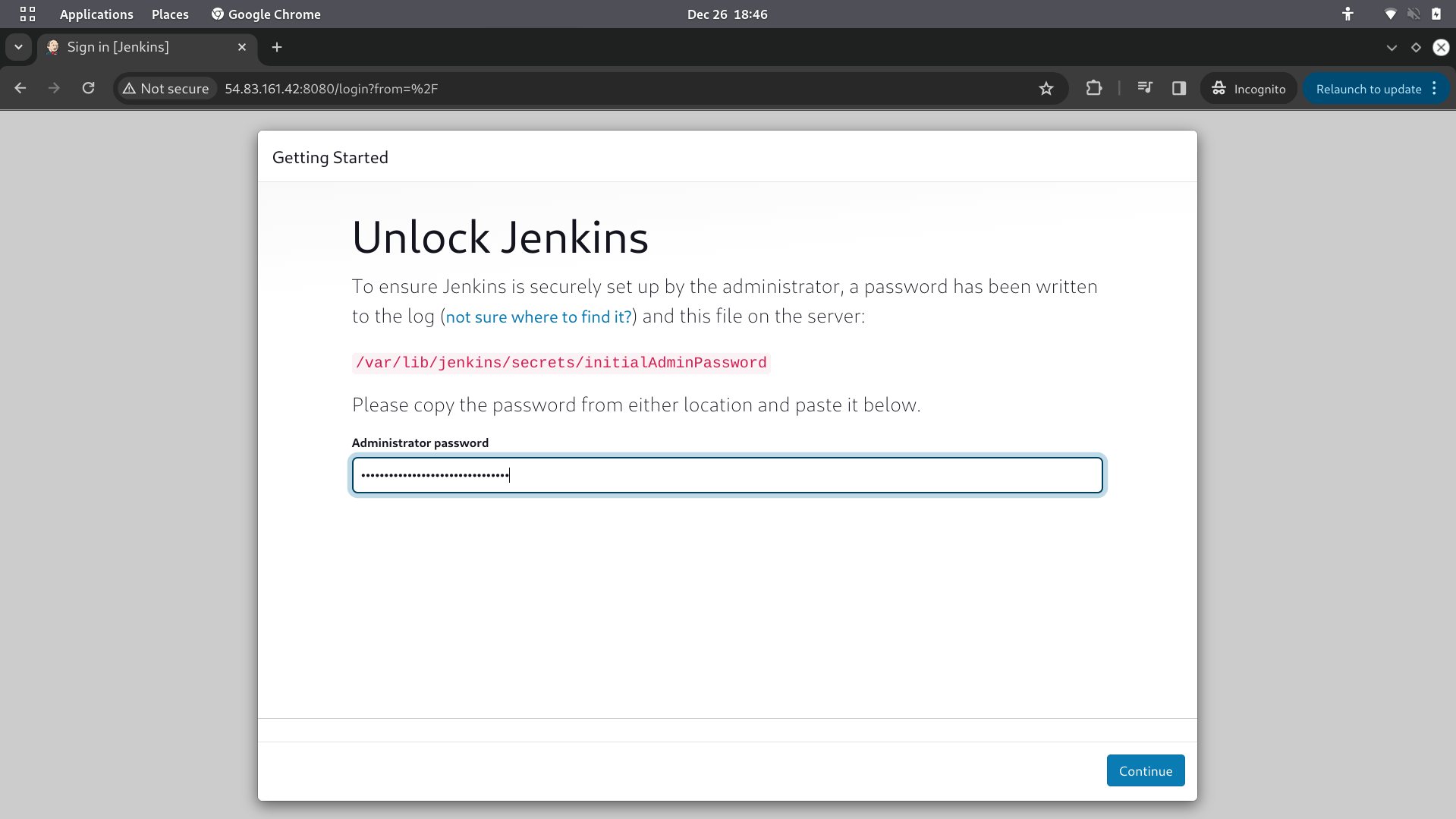
for Administrator password SSH into your jenkins instance and follow below steps
sudo su
cat /var/lib/jenkins/secrets/initialAdminPassword
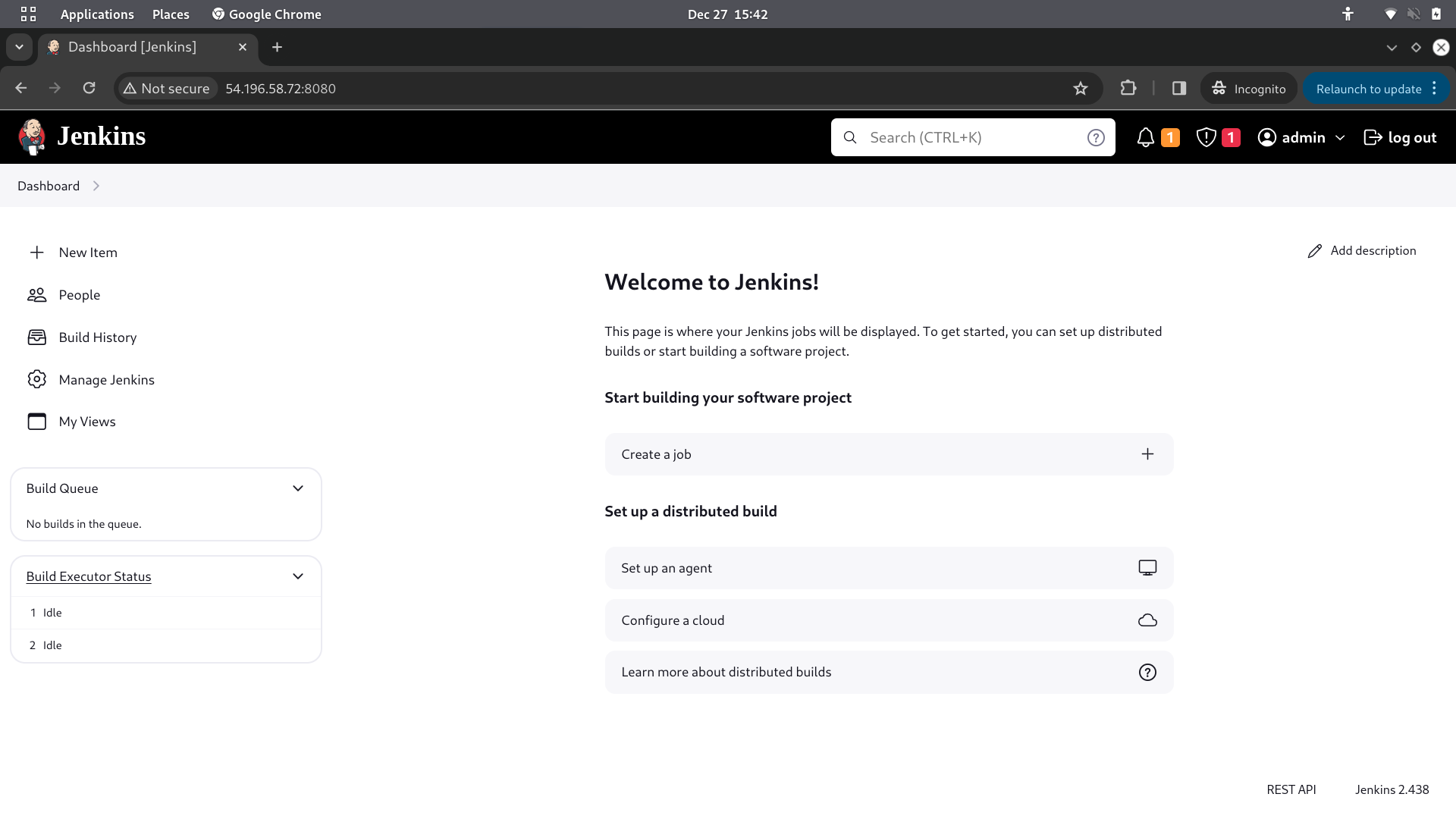
After creating new user — gets the Dashboard as shown in below snapshot
I want to do Jenkins deployment in EC2 using Terraform and this document helped me a lot. Thanks!
Fantastic tutorial on deploying Jenkins on EC2 using Terraform! The guide was incredibly detailed and easy to follow, with each step clearly explained. I appreciated the thoroughness in covering both the Jenkins setup and the Terraform configuration. Thanks to your clear instructions, I was able to successfully deploy Jenkins on EC2 without any issues. This guide is a valuable resource for anyone looking to streamline their Jenkins deployments using Terraform.
Awesome guide! The step-by-step process for Jenkins deployment on EC2 using Terraform was clear and easy to follow. I successfully set it up without any issues. Thanks for the great instructions!